Embedded Linux Security
Based on Introduction to Embedded Linux Security - part 1 and Introduction to Embedded Linux Security - part 2
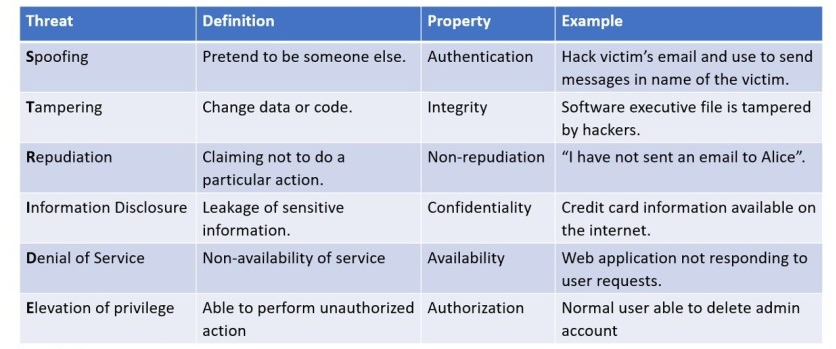
- STRIDE:
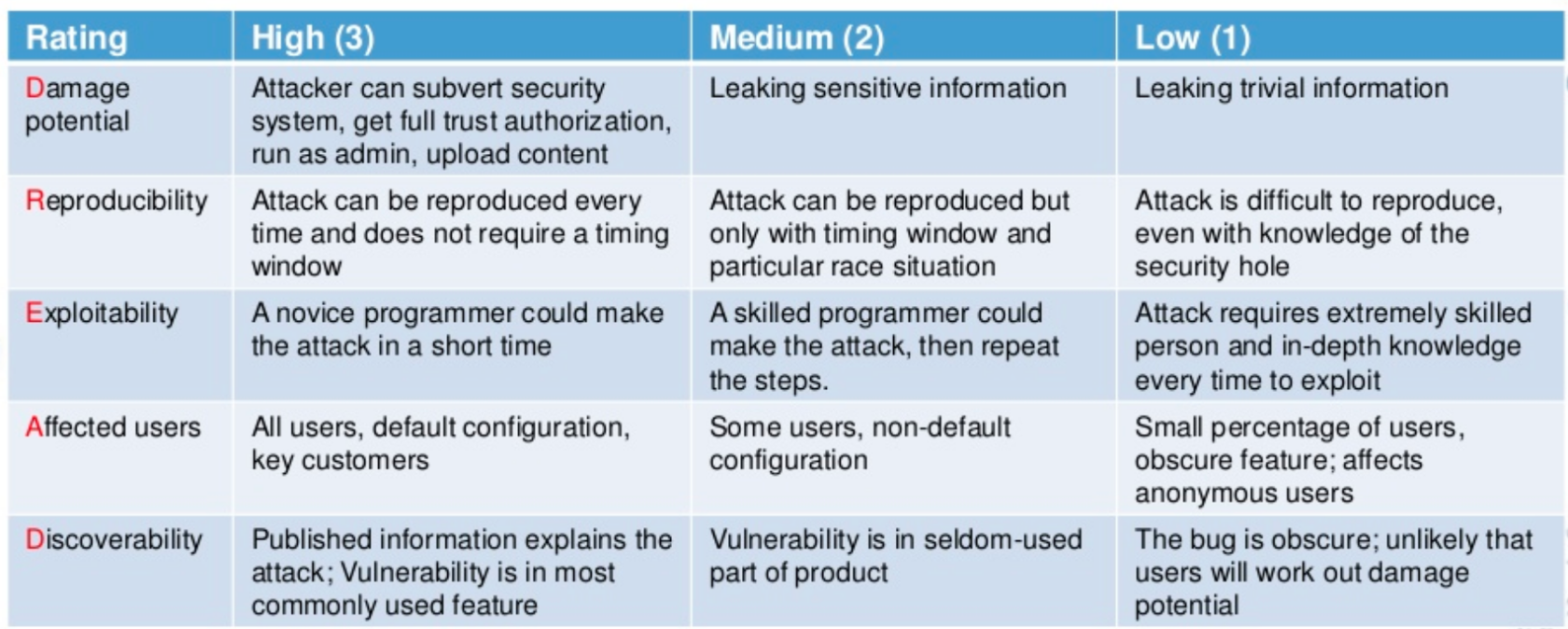
- DREAD:
- Secure Element: A Secure Element is a secure computing system. It is basically secure storage with its own secure applications (usually implemented using Java Card, but not necessary). What a secure element does is very open and depends on the implementation, but most of them implement the Public-Key Cryptography Standard 11 (PKCS#11). Examples of Secure Elements are smart-cards and SIM-cards.
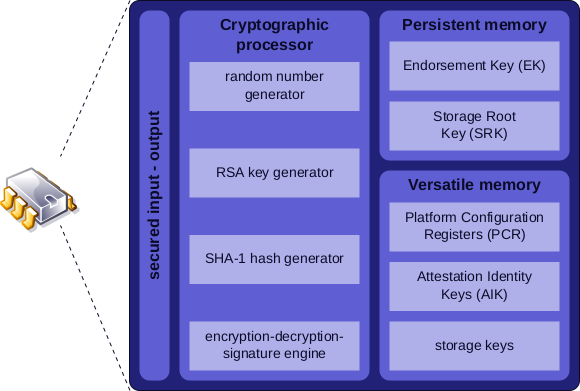
- TPM: A TPM (Trusted Platform Module) is a specification and an international standard (ISO/IEC 11889). TPM is not a Secure Element, although it could be implemented inside one. It can be implemented in hardware or software, but most implementations are in hardware. It provides a set of limited security features defined by the standard, including secure storage and cryptographic functions.
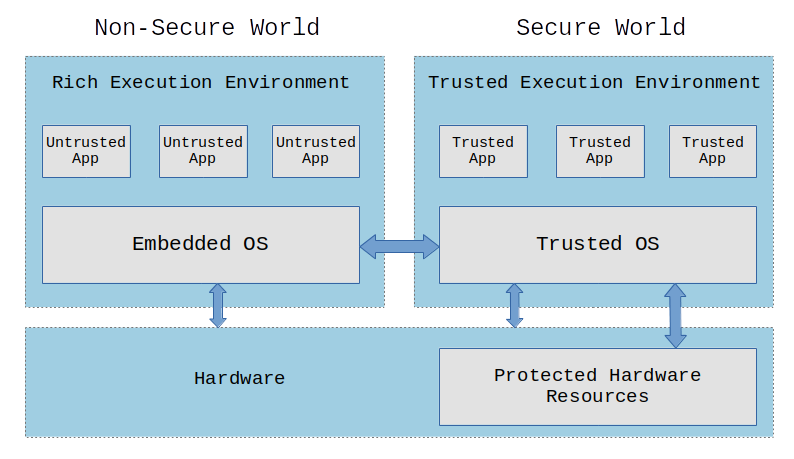
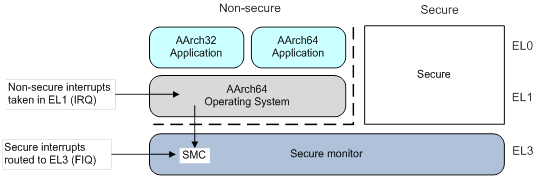
- TEE: A third alternative for secure storage would be using a Trusted Execution Environment. A TEE is an environment where the code executed and the data accessed is isolated and protected in terms of confidentiality (no one has access to the data) and integrity (no one can change the code and its behavior). A lot of devices around us make use of a Trusted Execution Environment, including smartphones, set-top-boxes, videogame consoles and Smart TVs. If you want more details about how a TEE works you can read my article “Introduction to Trusted Execution Environment and ARM’s TrustZone”.
More links
- Seccomp: Sandboxing in Linux with zero lines of code
- Trusted Platform Module (TPM): Introduction to TPM (Trusted Platform Module)
 ![[Pasted image 20250530152701.png]]
![[Pasted image 20250530152701.png]] - TEE / ARMs TrustZone: Introduction to Trusted Execution Environment and ARM's TrustZone
No Comments